The Key to Digital Security: Unveiling the Enigmatic World of Online Protection

In the vast expanse of the digital realm, the preservation of our online privacy and security has emerged as a pressing concern. 'The Key to Digital Security' serves as an indispensable guide, illuminating the intricate mechanisms of digital security and its profound significance in the modern era.
Section 1: Decrypting the Layers of Digital Security
1.1 Encryption: The Guardian of Sensitive Data
Encryption stands as the cornerstone of digital security, concealing confidential information in an impenetrable code that only authorized individuals can decipher. It operates akin to a virtual fortress, safeguarding our passwords, financial details, and other sensitive data from prying eyes.
4.5 out of 5
| Language | : | English |
| File size | : | 1518 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 316 pages |
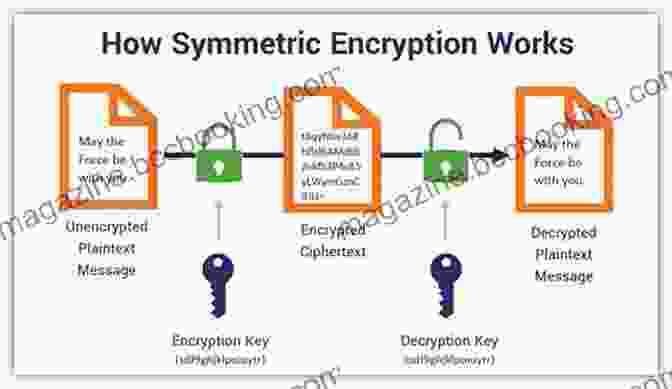
1.2 Authentication: Verifying Digital Identities
Authentication plays a crucial role in verifying the legitimacy of users accessing online platforms. Be it through passwords, biometric scans, or multi-factor authentication, these measures ensure that only authorized individuals gain access to sensitive accounts and data.
1.3 Security Protocols: The Rules of Online Communication
Security protocols govern how data is transmitted and exchanged across networks, establishing a framework of rules for secure communication. Protocols such as HTTPS and TLS encrypt data during transit, shielding it from potential eavesdropping or tampering.
Section 2: The Anatomy of Malicious Cyber Threats
2.1 Malware: The Digital Plague
Malware, encompassing viruses, Trojans, and ransomware, wreaks havoc on digital systems, ranging from data theft to disruption of operations. These malevolent software can infect devices through various vectors, such as phishing emails or malicious downloads.
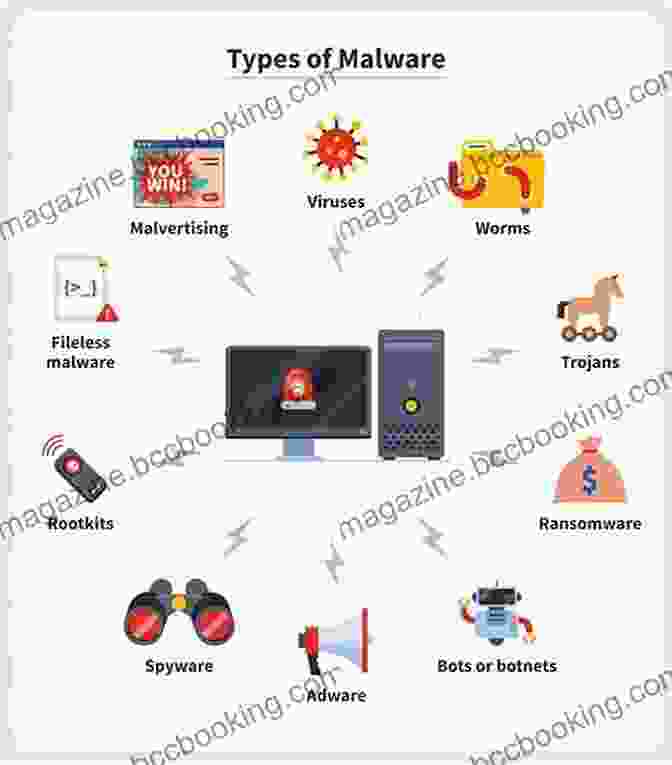
2.2 Phishing: The Art of Deception
Phishing, a prevalent cyber threat, employs deceptive emails, messages, or websites to trick individuals into divulging sensitive information, often leading to account compromise or financial loss.
2.3 Data Breaches: The Erosion of Trust
Data breaches occur when unauthorized individuals gain access to sensitive data stored by organizations, compromising the privacy of individuals and the reputation of the businesses involved. Understanding the causes and consequences of data breaches is essential for mitigating these threats.
Section 3: Essential Practices for Digital Security
3.1 Password Management: The Foundation of Data Protection
Creating and managing strong, unique passwords for each online account is a non-negotiable element of digital security. Password managers can assist in generating and securely storing these credentials.
3.2 Software Updates: Patching the Digital Leaks
Regularly updating software and operating systems is crucial for addressing security vulnerabilities. These updates often include patches that fix known weaknesses, preventing attackers from exploiting them.
3.3 Two-Factor Authentication: Enhancing Security with an Extra Layer
Two-factor authentication adds an additional layer of protection by requiring a secondary verification method, such as a code sent to a mobile device, alongside a password. This makes it significantly harder for unauthorized individuals to access your accounts.
Section 4: The Importance of Digital Security for Individuals and Organizations
4.1 Identity Protection: Shielding Your Online Persona
Digital security empowers individuals to protect their online identities from theft and fraudulent activities. By safeguarding personal information and credentials, you preserve your reputation and financial well-being.
4.2 Organizational Resilience: Mitigating Data Breaches and System Disruptions
For organizations, robust digital security measures are essential for preventing data breaches, safeguarding sensitive information, and maintaining operational continuity. Failure to implement adequate security can lead to catastrophic consequences for businesses.
'The Key to Digital Security' provides a comprehensive roadmap for navigating the complexities of the digital security landscape. By comprehending the mechanisms of encryption, authentication, and security protocols, as well as the prevalent threats posed by malware and phishing, individuals and organizations can effectively safeguard their digital assets. Embracing essential security practices and recognizing the profound importance of digital security empowers us to navigate the online world with confidence and protect our online presence.
4.5 out of 5
| Language | : | English |
| File size | : | 1518 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 316 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Max Adams
Max Adams Porochista Khakpour
Porochista Khakpour Kenneth W Noe
Kenneth W Noe Sharon Farritor Raimondo
Sharon Farritor Raimondo Stacey Matthews
Stacey Matthews Keith Crowley
Keith Crowley Ryan Pellett
Ryan Pellett Kevina Hopkins
Kevina Hopkins Laurent Martin
Laurent Martin Kerry Mcdonald
Kerry Mcdonald Nigel Cave
Nigel Cave Steve Griffith
Steve Griffith Stacy Tornio
Stacy Tornio Michaelbrent Collings
Michaelbrent Collings Michael Hurley
Michael Hurley Kelly Williams Brown
Kelly Williams Brown Kevin Sverduk
Kevin Sverduk Kathy Pike
Kathy Pike Sheri Van Dijk
Sheri Van Dijk Kris Rivenburgh
Kris Rivenburgh
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!
 Theodore Mitchell"Ed Roberts: Wheelchair Genius" by Tyler Hadyniak: A Beacon of Inspiration in...
Theodore Mitchell"Ed Roberts: Wheelchair Genius" by Tyler Hadyniak: A Beacon of Inspiration in...
 Jaime MitchellTest Prep With Practice Questions For The Navy Officer Aptitude Rating Exam
Jaime MitchellTest Prep With Practice Questions For The Navy Officer Aptitude Rating Exam Corey HayesFollow ·6.9k
Corey HayesFollow ·6.9k Braden WardFollow ·4.2k
Braden WardFollow ·4.2k Jackson HayesFollow ·2.1k
Jackson HayesFollow ·2.1k Victor HugoFollow ·12.6k
Victor HugoFollow ·12.6k Morris CarterFollow ·4.8k
Morris CarterFollow ·4.8k Robert ReedFollow ·9.4k
Robert ReedFollow ·9.4k Easton PowellFollow ·14.6k
Easton PowellFollow ·14.6k Michael ChabonFollow ·7k
Michael ChabonFollow ·7k

 Joshua Reed
Joshua ReedUnveiling the Profound Essence of Taekwondo: Spirit and...
Taekwondo, an ancient...

 Clarence Brooks
Clarence BrooksUnveiling Clarity: The Common Sense Guide to Everyday...
In the labyrinthine world of legal...

 Anthony Wells
Anthony WellsBless Me, Ultima: A Literary Odyssey into the Heart of...
In the tapestry of American literature,...

 Alexandre Dumas
Alexandre DumasPioneer Life Or Thirty Years A Hunter - A Captivating...
Discover the Raw and...

 Samuel Beckett
Samuel BeckettThe Mike Fisher Story: An Inspiring Tale of Faith,...
Prepare to be...
4.5 out of 5
| Language | : | English |
| File size | : | 1518 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 316 pages |